What is Cybersecurity and Why Should You Care?

From smartphones to smart homes, our growing dependence on technology has created vulnerabilities. Cybersecurity acts as a protective shield to our internet-enabled devices and data against these threats. It saves from evil motto attacks in the form of phishing scams, ransomware, data breaches, identity theft, and financial losses. At a time when cybercrime is rapidly increasing, knowledge of cybersecurity assumes immense importance to guarantee the safety of our digital lives. So, in today’s blog, we will be discussing about Cybersecurity in detail!!
Table of Contents
What is Cybersecurity?

Cybersecurity is the branch of computer science dealing with the protection of electronic devices and services against malicious attacks. Such attacks are normally carried out by hackers, spammers, and cybercriminals. While some cybersecurity measures are proactive in offense, for the vast majority of professionals, the robust defence will be the key area of operation. The postures developed would cater to a wide variety of assets, ranging from personal computers and smartphones to whole networks and databases. The term ‘cybersecurity’ is often used by the media to refer to all types of protection from digital crimes, ranging from identity theft to international cyber-attacks.
Also read: 20 Amazing Projects For Beginners to Start Coding
Importance of Cybersecurity

Cybersecurity will not be an option in our increasingly digitized world. One security breach may mean exposure to the personal information of millions of people, leading to huge financial losses for companies and a shaken customer base. Robust Cybersecurity practices should, therefore, protect both the business Enterprise and customers against these ever-present threats that spammers and cybercriminals pose.
Cybersecurity Elements
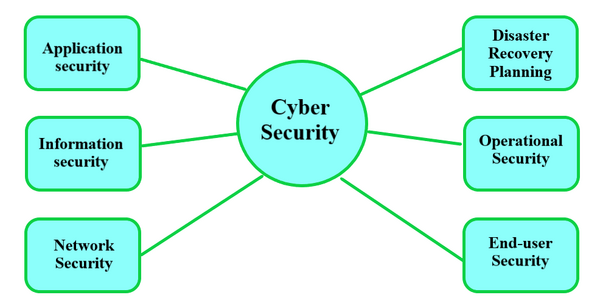
- Application Security: Secure code, design, and data input validation that prevent unauthorized access or modification of applications.
- Cloud Security: Setting up a secure cloud architecture and applications for those companies that make use of cloud service providers.
- Identity Management and Data Security: Mechanisms for authorization, authentication, and information protection that permit safe information storage.
- Mobile Security: Protection of organizational and personal information kept in mobile devices from a number of threats.
- Network Security: Hardware and software mechanisms put in place to protect the network and the infrastructure of any Corporate IT setup.
- Disaster Recovery and Business Continuity Planning: Processes and plans for the continuity of business-critical systems during and after incidents, and recovery of lost operations. User Education: Training staff in the basics of cybersecurity and best practices and how to report suspicious activities.
Cybersecurity threats types
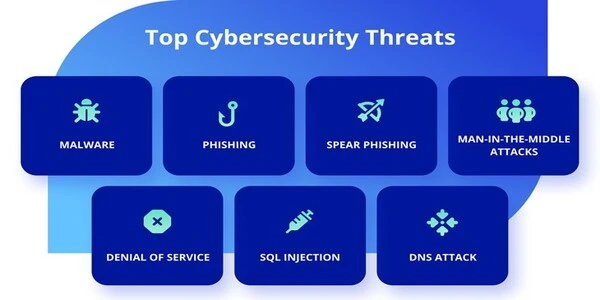
- Cyberterrorism: politically motivated attacks on computers to harm and engender chaos in society.
- Malware: It refers to any hostile software that can either steal data, block access, or even harm systems. Examples include ransomware, spyware, viruses, and worms.
- Trojans: These are benumbed files that appear to be something of interest so that when a user downloads and installs these keystroke loggers into their computer system, they attack the system.
- Botnets: Huge networks of unsecured devices, hijacked by criminals to badly attack systems.
- Adware: It is unwarranted software bombarding/flooding the user’s system with so many advertisements.
- SQL Injection: A hack that injects malicious code into a server to steal data.
- Phishing: Emails or correspondence designed to be deceptive and used to steal personal information or install malware.
- Man-in-the-Middle Attack: A hacker inserts himself or herself between online communications to steal data. This often happens on insecure Wi-Fi networks.
- Denial-of-Service Attack: This involves overwhelming a system with traffic to prevent it from responding to legitimate requests.
Pros of Cybersecurity

- Sensitive Data Protection: Cybersecurity actions include protecting sensitive data from unauthorized access, thus maintaining privacy and avoiding identity theft. This attracts data like social security numbers, credit card information, medical records, and personal emails.
- Business Continuity: Cyber attacks could very well result in business disruption and monetary loss. The same can be prevented with the help of cybersecurity measures that ensure businesses continue unabated even on being targeted.
- Compliance: Restrictions A lot of industries have regulations that require their businesses to protect customer data. Cybersecurity measures help businesses comply with regulations and avoid fines.
- Higher Level of Customer Trust: The customer wants to deal with a business that they feel is trustworthy to keep their data safe. This forms the base of establishing this trust by implementing cybersecurity measures within the organization.
- Competitive Advantage: These days, in a digital world, cybersecurity became known as an added competitive business advantage. Enterprises committed to strong cybersecurity stand to gain customers and partners.
- Early Detection and Response: Cybersecurity measures help organizations detect the cyber-attacks at an early stage and act promptly to reduce the potential damage.
- Protection of Intellectual Property: A lot of time and money goes into developing intellectual property. Cybersecurity measures help businesses protect this intellectual property against theft.
- Protection of Reputation: A cyber-attack can hamper a business’s reputation. Cybersecurity measures will ensure protection for a business in this regard.
- Improved Collaboration: With the prevailing global economy, sometimes companies are asked to collaborate with partners and customers who happen to be on opposite sides of the globe. Cybersecurity measures will allow sharing of sensitive data securely.
- Security in Remote Working: With the trend of increasing remote working, the need for effective cyber security measures within a business increases. Proper cyber security measures taken for the protection of the business can avoid or minimize targeted cyber-attacks.
Also read: How to get started with coding: a beginner’s guide to programming
Important Cybersecurity Practices
- Don’t just click! Hover over links to see the real destination URL before you visit.
- Strong and unique passwords are your first line of defense. Don’t be lazy, create passwords that would stump a superhero!
- External drives and USB sticks can be malware magnets. Scan them before plugging them in.
- Store sensitive information like passwords and financial documents securely, not on sticky notes or easily accessible files.
- Double up your security with two-factor authentication (2FA) wherever possible. It’s like having a secret handshake to log in.
- Look for the https:// at the beginning of website addresses. This “S” means the site encrypts your data, making it harder for prying eyes to see.
- Annoying pop-ups and unwanted ads can be more than a nuisance, they can be security threats. Scan for and remove adware to keep your computer clean.
- When you’re not using Bluetooth, turn it off. It creates a potential pathway for hackers to access your device.
- Avoid using public Wi-Fi that is not secure for sensitive activities such as online banking. If you must use it, consider a VPN (Virtual Private Network) for added protection.
- Consider security software upgrades to keep your defences up-to-date against the latest threats.
- Ethical hackers, also known as white hat hackers, can help identify vulnerabilities in your systems before bad guys do.
Cybersecurity Safety Tips
- Stay ahead of security threats: Regularly update software to patch vulnerabilities.
- Be mindful of emails: Don’t open suspicious emails to avoid malware or phishing attacks.
- Shield your devices: Use antivirus and anti-malware software to actively protect your devices.
- Encrypt sensitive information: Securely share data using a file-sharing solution with encryption.
- Create strong, unique passwords: Make them hard to guess and use different passwords for each account.
- Safeguard your data: Regularly back up your important information to prevent loss.
- Spot and avoid phishing attempts: Be cautious of emails or messages trying to trick you into revealing personal information.
- Simplify strong password management: Use a password manager to create and store complex passwords.
- Add an extra layer of security: Enable two-factor authentication for an additional login step.
- Never reuse passwords: This strengthens your overall security posture.
Conclusion
Cybersecurity isn’t just for tech giants and government agencies. In today’s digital world, everyone – individuals, families, and businesses – has a stake in protecting their online information and devices. By understanding cybersecurity threats and taking steps to mitigate them, you can safeguard your privacy, finances, and even your physical safety. Remember, cybersecurity is an ongoing process, but a little vigilance goes a long way in keeping yourself secure online.
Also, check:
FAQs
1. What is cybersecurity?
Cybersecurity involves safeguarding systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It’s essentially a set of strategies to keep your online information safe from cyber-attacks.
2. What are some common cyber threats?
There are many, but some of the most common include phishing scams, malware (including viruses and ransomware), hacking attempts, and data breaches.
3. Why should I care about cybersecurity?
A cyber-attack can have serious consequences. It could lead to identity theft, financial loss, damage to your reputation, or even disruption to critical infrastructure.
4. What can I do to improve my cybersecurity?
There are many steps you can take, such as using strong passwords and keeping software updated, being cautious about opening emails and clicking links, and being mindful of what information you share online.
5. Where can I learn more about cybersecurity?
There are many resources available online and from government agencies. A good place to start is the National Institute of Standards and Technology (NIST) Cybersecurity Framework


